To remove any newly installed application, you always need to use an uninstall program. This program is not a feature of Windows system. Every software application comes with its own unisntall feature. Or at least you hope it does.
Usually uninstall programs are on the Start button’s All Programs menu, right by the icon used to open the application. For instance, the command to remove the application is called, remarkably, “Uninstall”. This kind of setup is common for most applications.
If your software lacks an obvious uninstall option/program, you may attempt to use Windows to rid yourself of it: Directly access the Control Panel’s Add or Remove Porgram/Uninstall a program icon to witnees for yourself the glory taht is the Add or Remove Program Properties dialog box.
The list of programs that Windows knows about and can remove is listed in the dialog box, as you can see in the image. Click on one of those programs, the one you want to remove, and then click the Change/Remove button or double-click the program item. Continue reading wizard Instructions on the screeen to remove the program.
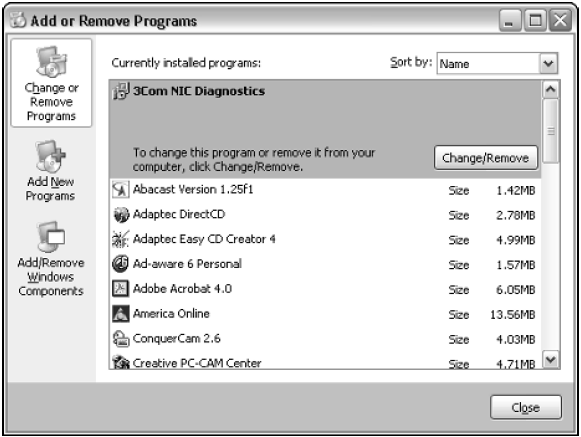
Do not attempt to remove any software by deleting it from your hard drive, like simply dragging the folder to Recycle Bin. You shall never delete any file you did not creat yourself. However, you can delete any shortcuts you create.
Some stubborn applications do not fully uninstall themselves. If you have tried everything, feel free to kick out the program by deleting its icon or folder. However, do not delete any application or file installed in the Windows folder or any of its sub-folders.









Recent Comments